Cybersecurity Awareness
Find information on cybersecurity awareness topics.
Cybersecurity Training
UCOP
UCOP features several Cybersecurity events each year to help you stay safe online. Find the latest information and trainings on their security page:
- Data Security Month, January
- Cybersecurity Awareness Month, October
- Information Technology Policy and Security Community of Interest, monthly
- UC Cybersecurity Summit
UC San Diego
- Guiding Principles for Personal Data held by UC San Diego
- Privacy Education
- Privacy 101 training
- On-demand Privacy @ UC San Diego training
- General Data Protection Regulation (GDPR) Seminar
Ways to stay safe online
By learning the four simple steps we can take to stay safe online at home, work and school, and sharing these tips with our community, we can all become significantly safer online.
Below are the simple actions we should all take not only during October but every day throughout the year.
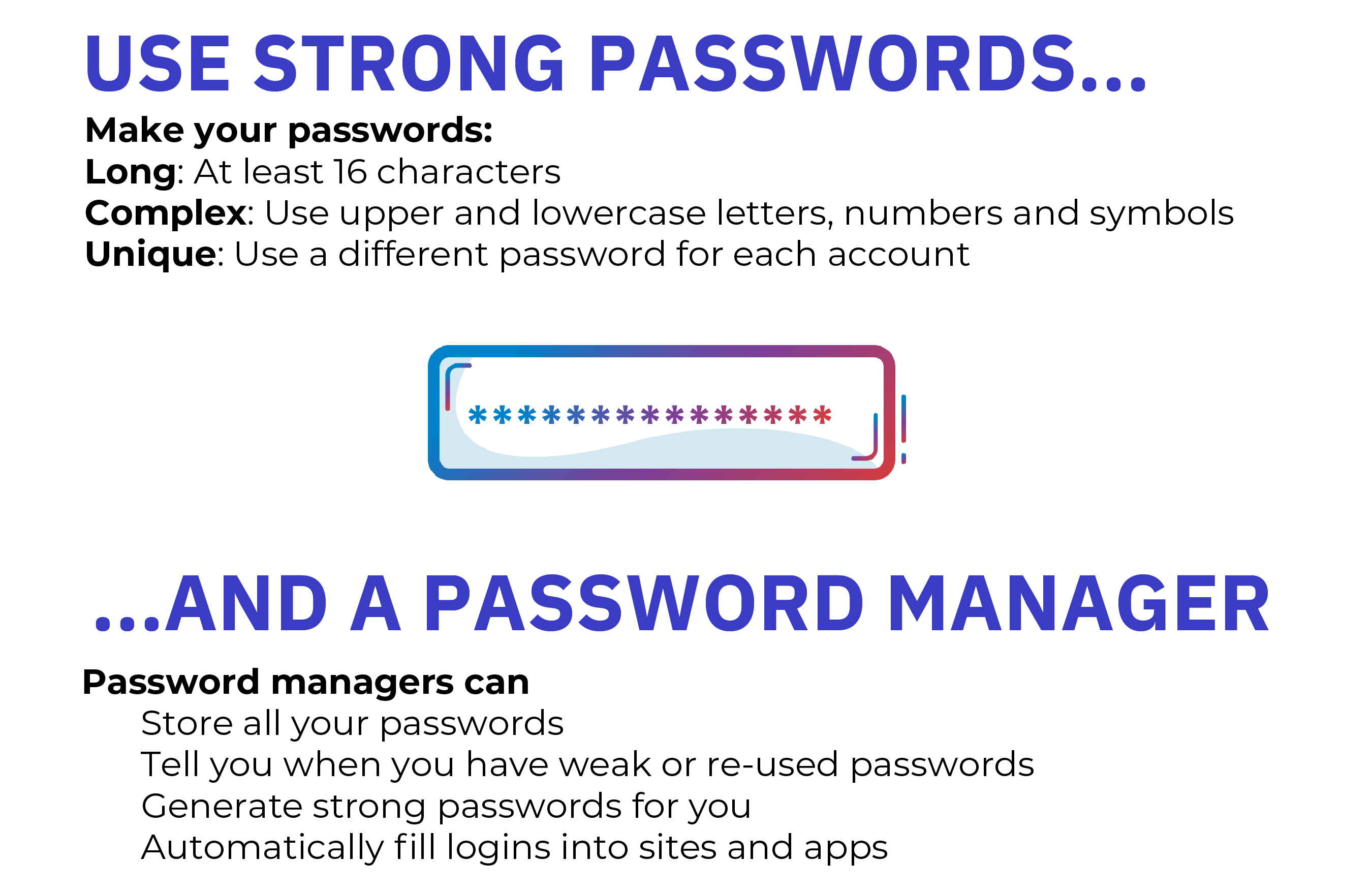
1. Use Strong Passwords and Password Manager
As our online lives expand, the average user has gone from having just a few passwords to now managing upwards of 100. That’s 100 unique passwords to remember if you’re using strong password habits. Password managers can save users the trouble of having to remember multiple passwords and make accounts safer by recommending strong, unique passwords and storing them all in one place.
OUR TIPS AND ADVICE
Using an easy-to-guess password is like locking the door but leaving the key in the lock. Weak passwords can quickly be cracked by computer hackers. The good news is that strong passwords are one of the easiest ways to protect your accounts from compromise and reduce the risk of someone stealing sensitive information, data, money, or even your identity.
STRENGTHEN YOUR PASSWORDS WITH THESE TIPS
1. Longer is stronger: Passwords with at least 16 characters are hardest to crack.
2. Hard to guess: Use a random string of mixed-case letters, numbers and symbols. If you need to memorize a password, create a memorable “passphrase” of 5 – 7 unrelated words. Get creative with spelling and/or add numbers or symbols
3. One of a kind: Use a unique password for each account.
Remembering long, unique passwords for every account in our lives is impossible. Rather than write them down or reuse weak passwords, use a password manager.
Password managers generate complex and unique passwords for you, store them all in one place and tell you when you have weak, re-used passwords, or compromised passwords. They can also automatically fill credentials into sites and apps using a secure browser plugin. You only need to remember one master password—the one for accessing the password manager itself. (Tip: Create a memorable long “passphrase” as described above and NEVER write your master password down.)
ADDITIONAL FACTS AND FIGURES
- Only 33% of individuals create unique passwords for all accounts (NCA)
2. Turn On Multifactor Authentication (MFA)
In a recent National Cybersecurity Alliance survey, 57% of respondents said they have heard of multifactor authentication (MFA), but many people don’t realize that multifactor authentication is an incredibly important layer of protection in keeping accounts secure. This month, we’re showing others how easy it is to turn on MFA whenever possible.
OUR TIPS AND ADVICE
MFA provides extra security by providing a secondary method confirming your identity when logging into accounts. MFA usually requires you to enter a code sent to your phone or email, or one generated by an authenticator app. Push notifications are also common methods of MFA. This added step prevents unauthorized users from gaining access to your accounts, even if your password has been compromised.
FOLLOW THESE STEPS TO TURN ON MFA
- Open your app or account settings
- It may be called Account Settings, Settings & Privacy or similar.
- Turn on multifactor authentication
- It may also be called two-factor authentication, two-step authentication or similar.
- Confirm
- Select an MFA method to use from the options provided. Examples are:
- Receiving a code by text or email
- Using an authenticator app: These phone-based apps generate a new code every 30 seconds or so.
- Biometrics: This uses facial recognition or fingerprints to confirm your identity.
- Select an MFA method to use from the options provided. Examples are:
ADDITIONAL FACTS AND FIGURES
- Of those who have heard of MFA, 79% had applied it to their online accounts. (NCA) )
- Of that number, 94% said they are still using MFA, showing that once MFA is enabled, users will keep using it. (NCA)
3. Recognize and Report Phishing
OUR TIPS AND ADVICE
Phishing occurs when criminals try to get you to open harmful links or attachments that could steal personal information or infect devices. Phishing messages or “bait” usually come in the form of an email, text, direct message on social media or phone call. These messages are often designed to look like they come from a trusted person or organization, to get you to respond. The good news is you can avoid the phish hook and keep accounts secure!
1. Recognize - Look for these common signs:
- Urgent or alarming language
- Requests to send personal and financial information
- Poor writing, misspellings, or unusual language
- Incorrect email addresses, domain names, or links (e.g. amazan.com)
2. Report - If you suspect phishing, report the phish to protect yourself and others.
- Know your organization’s guidance for reporting phishing. If your organization offers it, you may find options to report via the “report spam” button in your email toolbar or settings.
- For personal email accounts, you may be able to report spam or phishing to your email provider by right-clicking on the message.
3. Delete - Delete the message. Don’t reply or click on any attachment or link, including any “unsubscribe” link. Just delete.
ADDITIONAL FACTS AND FIGURES
- 72% of respondents reported that they checked to see whether messages were legitimate (i.e. phishing or a scam) compared to 15% who reported not doing so. (NCA)
- 47% of the participants said they used the reporting capability on a platform (e.g. Gmail, Outlook) “very often” or “always”. (NCA)
4. Update Your Software
Approximately 2 in 5 survey respondents say they either “sometimes,” “rarely,” or “never” install software updates (NCA). One of the easiest ways to protect accounts and information is to keep software and applications updated. Updates are periodically released to fix software problems and provide security patches for known vulnerabilities. This Cybersecurity Awareness Month, don’t hit the “remind me later” button. Take action to stay one step ahead of cybercriminals.
OUR TIPS AND ADVICE
Keeping software up to date is an easy way improve your digital security. For added convenience, turn on the automatic updates in your device or application security settings! Set it and forget it!
KEEP SOFTWARE UP TO DATE WITH THESE STEPS:
1. Check for notifications
Devices and applications will usually notify you when the latest software updates become available, but it’s important to check periodically as well. Software updates include devices’ operating systems, programs and apps. It’s important to install ALL updates, especially for web browsers and antivirus software, or apps with financial or sensitive information.
2. Install updates as soon as possible
When a software update becomes available, especially critical updates, be sure to install them as soon as possible. Attackers won’t wait, and you shouldn’t either!
3. Turn on automatic updates
With automatic updates, devices will install updates as soon as they become available—Easy! To turn on the automatic updates feature, look in the device settings, usually under Software or Security.
ADDITIONAL FACTS AND FIGURES
- 36% of survey participants reported installing the latest updates and software as soon as they became available. (NCA)
- Of those who reported installing the latest updates to their devices, 62% had turned on automatic updates. (NCA)