Can customers opt-out (if they don't like the reformatting issues, for example)?
There is no opt-out process in place.
Will the links still work after some indefinite period of time? (such as when Proofpoint isn't the low bidder for the next renewal - or does that make for permanent lock-in) or Proofpoint is unreachable?
The links will work indefinitely, even if we cease being a Proofpoint customer.
Will Proofpoint's visiting the site to scan it before redirecting the customer invalidate one-time use URLs (like password reset messages or redeem-once offers) before the customer sees them?
No, it will not invalidate one-time use URLs because Proofpoint does not visit the site, the URL is rewritten. The first visit occurs when the customer clicks on the rewritten link, and it is at that time, the site link is evaluated.
Will forwarding a message with the rewritten links make your outgoing messages look more spammy to some third-party anti-spam solution that's used by a third-party recipient because the links point to some weird location that appears unconnected with the title of the link?
This should not be an issue; it was not experienced during testing. That said, if problems arise during a broader roll-out, we will address the issue as soon as we are notified.
Does Proofpoint log and/or track link visiting activity?
Proofpoint will log when someone clicks a link. That is the extent of logging. This information is given to UC San Diego to identify any account clicked on with a malicious link that previously was not considered malicious. At this point, the security office can follow up with that individual to ensure their credentials are not compromised.
What info is encoded in the long random-looking strings? Is it unique/traceable back to individual emails, or will a link to ucsd.edu always be encoded the same?
The encoding includes the original link, the original recipient, and a security identifier that links it to the UC San Diego instance of Proofpoint.
Will PGP signed messages be invalidated due to the rewriting?
Only HTML PGP signed messages received from a non-campus email account or via our campus mailing list would be invalidated. Plaintext PGP signed messages would not have links rewritten and will not be invalidated.
If it doesn't impact Exchange to Exchange messages, how will this help with compromised campus accounts sending spam to other customers? (Other than by possibly reducing the number of compromised accounts)
This isn't perfect, no. Typically we see a phishing message come in from outside campus; somebody falls for it, and then it bounces around inside Exchange. If we can prevent patient zero (or reduce the number of patient zeros), we'll be in a much better position. But in the future, we should look at strengthening other protections, including those within Exchange. There are also additional protections in place that help in this area.
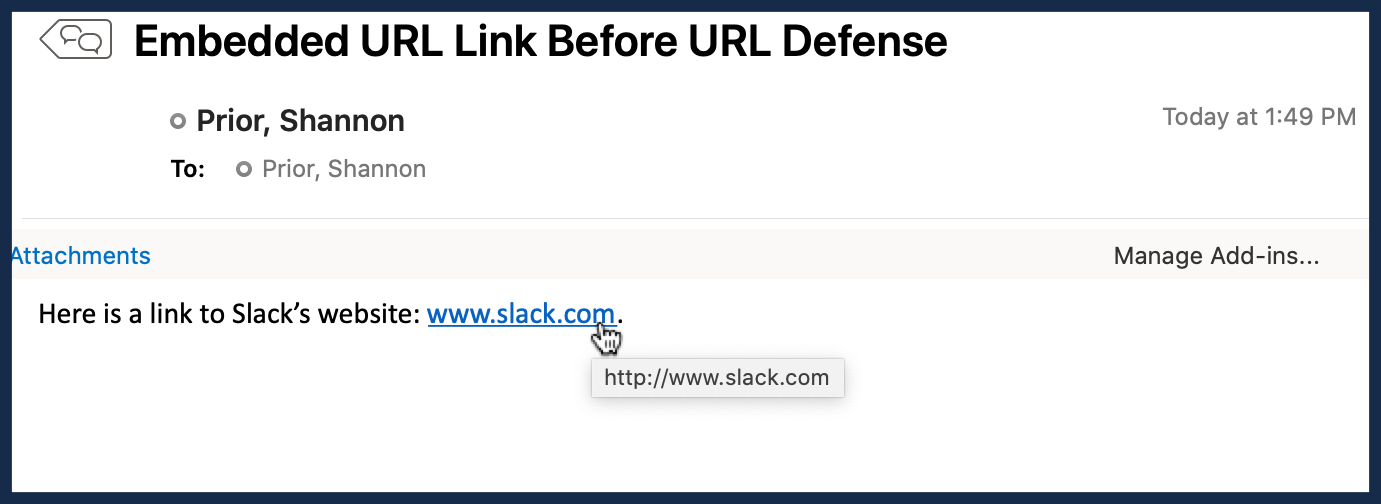
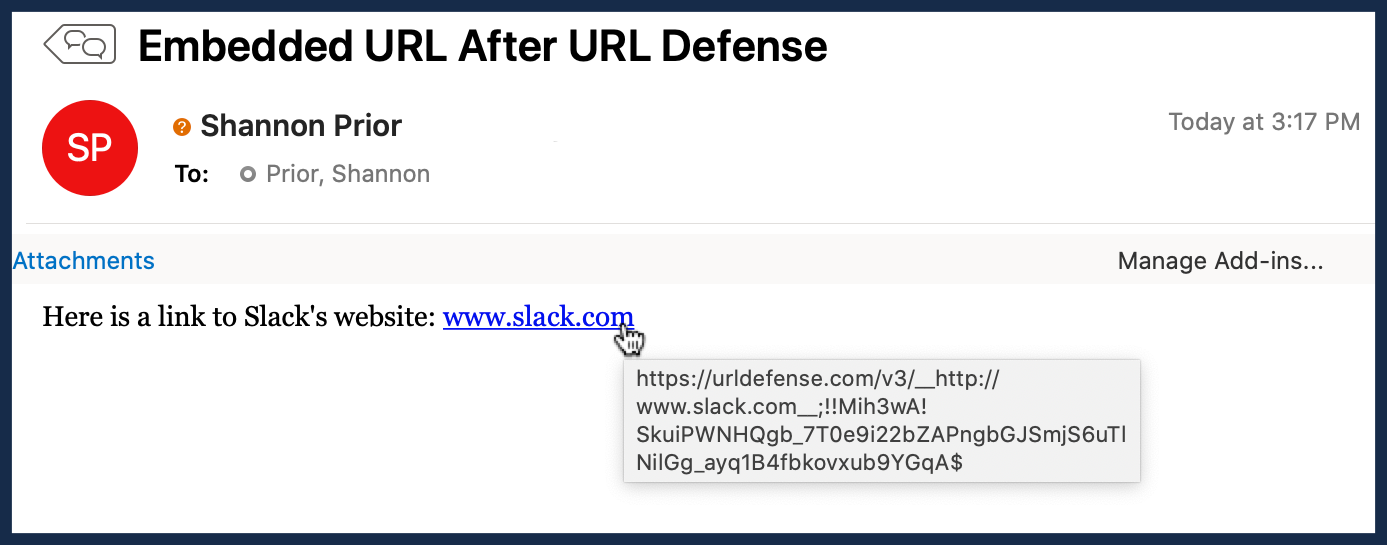
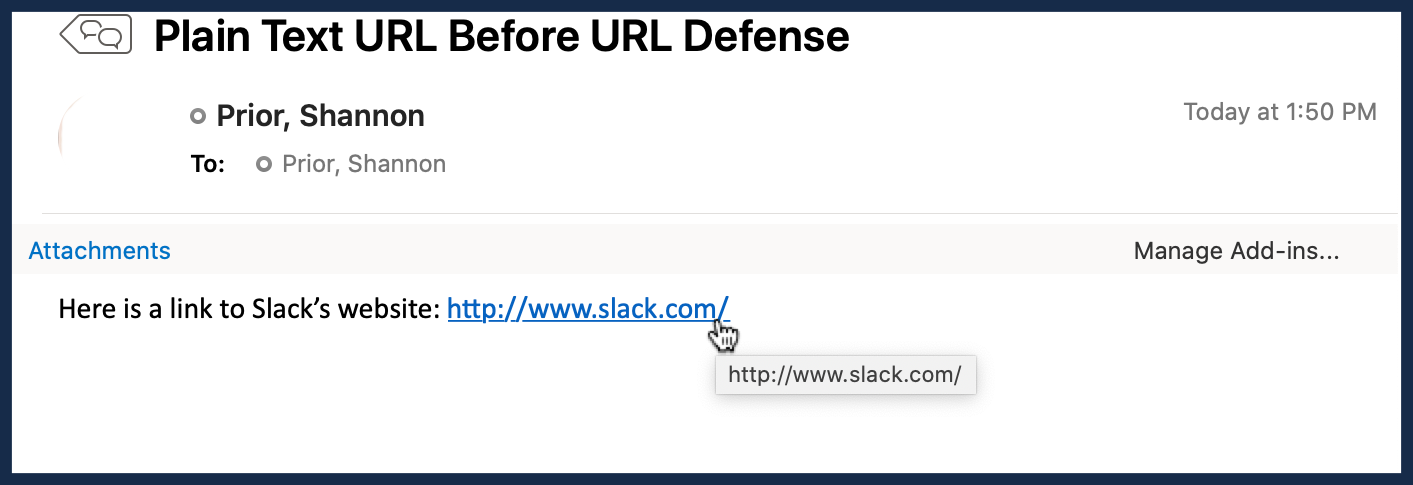
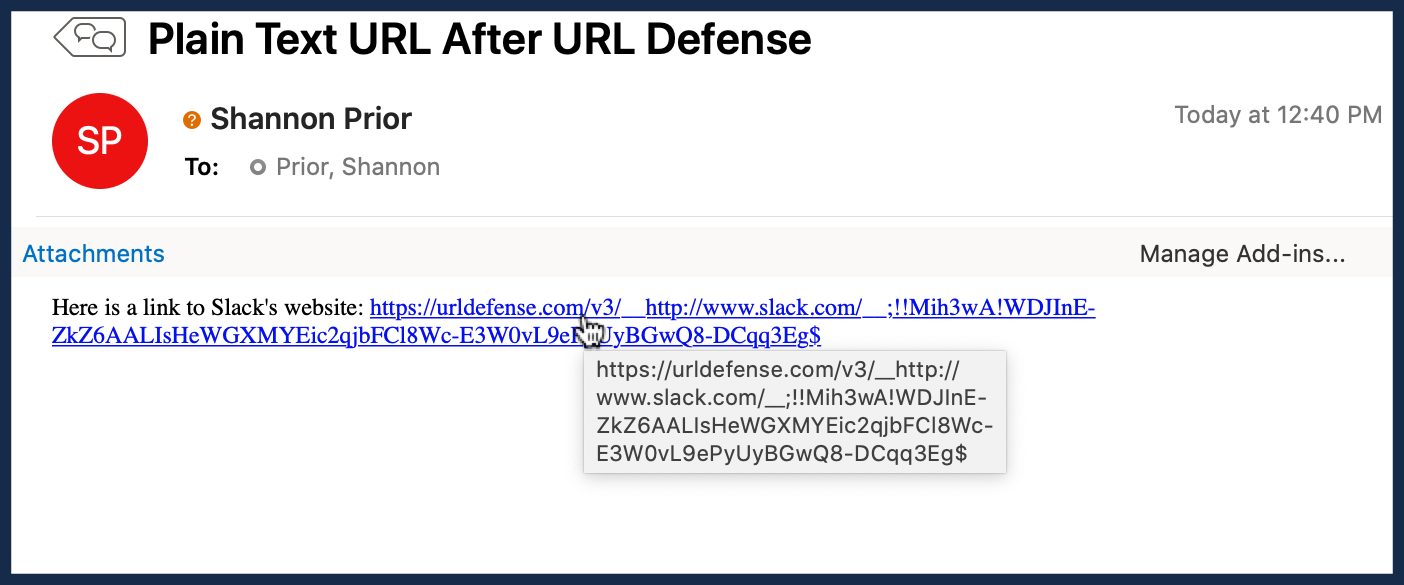
I've been taught to hover over the link in the email to make sure the web address matches the link. Does this mean I shouldn't do this anymore?
We realize this will introduce complexity for you. It's not ideal. But given the number of compromised accounts we see because people aren't checking links, this seems to be an appropriate response. Part of the reason we're going with the URL labeling instead of the straight link rewriting is to better educate the readers to where a link is going to take them (which is more than they're getting right now). And we are telling people to look for the Proofpoint URL if they do the hover over (for the few who do).
I use Thunderbird, and messages are now flagged as junk. Is this a result of URL rewriting?
We have seen some reports of this, although we have not been able to track down an exact resolution. You can try tweaking settings per email account in Junk Settings under Account Settings to see if this helps.